Threats and Vulnerabilities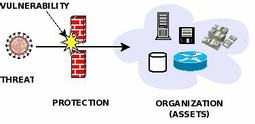
As the picture illustrates, threats are very different than vulnerabilities. A vulnerability is a weakness in the protection efforts and mechanisms. Risk is the potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. Risk is the intersection of assets, threats, and vulnerabilities. In this environment, there are bad actors who develop and deploy threats with bad intentions and there are those who develop the protection mechanisms to protect assets. Those who are in the protection business need to have an understanding of the threats and the vulnerabilities in order to protect the organization's assets. Threats come in the form of both cyber and physical domains. In order to protect the assets, from both attack domains, the organization needs to develop a culture of continuous learning to stay current on both threat vectors.
One method for understanding threats and vulnerabilities is the adoption of penetration testing. A penetration test, or sometimes pen-test, is a software attack on a computer system that looks for security weaknesses, potentially gaining access to the computer's features and data. The process typically identifies the target systems and a particular goal, then reviews available information and undertakes various means to attain the goal. The act of pen-testing involves deliberate attacks on the protection mechanisms which becomes an ethical question. Is this legal? Those who poses the skills to conduct the pen-testing are often performing the same tasks utilizing the similar tools. The difference is that pen-testers are authorized to conduct the test. Fundamentals in cybersecurity span a wide number of topics. I elected to include only a few but I view these as being highly relevant from a professional and ethical perspective. The first artifact is a vulnerability assessment plan. This provides senior managers basic understanding of the three core elements to conducting a vulnerability assessment. Also included in this artifact is a sample assessment of a vulnerability test conducted against a network. The next artifact is a threat statement table. This is designed for senior leaders to begin to view their threats in discrete elements. It is easy to see how the complexity of large organizations can obfuscate and distort threats. They can often be viewed as a single morass of concerns. By cataloging and categorizing threats into discrete elements, the organization can work towards addressing the threats with an organized approach. The final set of artifacts are more tactical but illustrate how the threats are modeled and security personnel can be trained. Tools like Metasploitable are opensource and available to anyone; even the bad guys. However, security teams who are authorized are operating within the ethical boundaries of the profession and the law with the purpose to identify vulnerabilities to protect company assets. |
Examples and ArtifactsVulnerability Assessments (VA) - Is a risk management process used to identify, quantify and rank possible vulnerabilities to threats in a given system. It is not isolated to a single field and is applied to systems across different industries, such as: IT systems. A vulnerability assessment can be conducted across the phases: (Click here for a sample)
Threat Statement Tables - Threat statement tables are used to catalog threats to the organization. The tables describe the class of threat, description and the impact to the confidentiality, integrity and availability to the organization. Click here to view sample.
Simulating DoS attacks with Metasploitable - Metasploitable is an intentionally vulnerable Linux virtual machine that can be used to conduct security training, test security tools, and practice common penetration testing techniques. This is an example of a DoS attack that emulates the SlowLoris Attack. Click here to see how this works in Metasploitable. Simulating DoS attacks with Python - Python is an interpreted high-level programming language for general-purpose programming. Security professionals like working with Python because it is easy to learn, versatile, wide-usage and extensive support libraries to cite a few. This program is in two parts; client and a server. The server has a capacity of 5 clients. The client program automatically logs into the server 5 times. This is often referred to as multi-threading. The DoS attack happens when the client attempts to log-in to the server 6 times, thus causing a denial of service. It is a rudimentary example but illustrates exactly how easy it is to cripple a server. Click here for the code and sample output. |