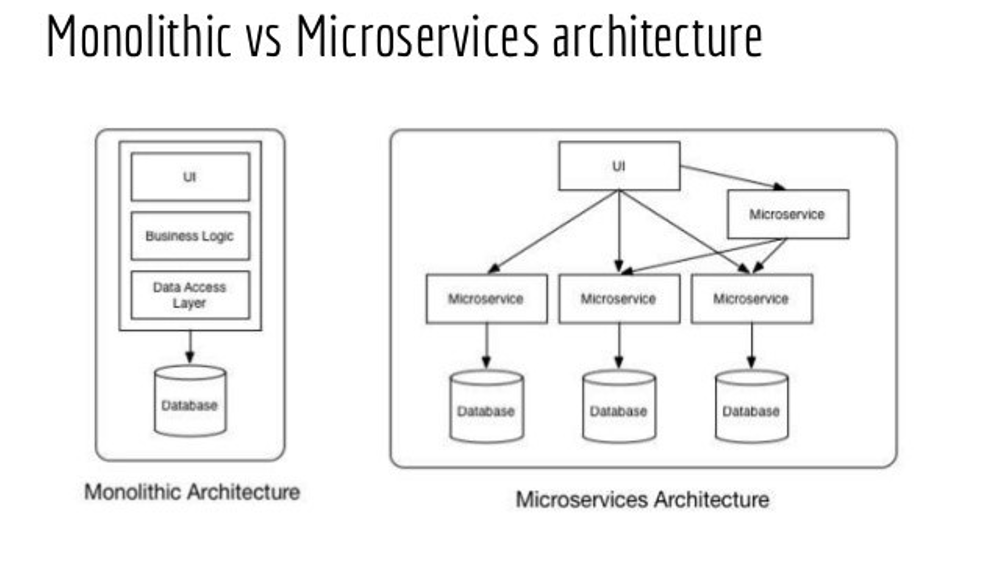
1. Componentized versus MonolithicMonolithic systems in general are a bad idea. With the possible exception of Enterprise Resource Planning (ERP) where tight integration among business processes like sales orders, inventory, manufacturing and financial reporting is a big advantage. However, in the field of security, technologies are improved and new standards are released. This makes a monolithic approach difficult to maintain and potentially unsafe.
Application Programming Interfaces (API’s) are used to call services from other programs. If the service is embedded within a larger, monolithic application, it is much harder to upgrade it if the technology changes. In a componentized architecture; where API’s are used, the API simply points to the new service. This becomes much easier to understand, maintain and test. |
2. Interoperability vs Latest TechnologiesLatest technologies are important, however, if they cannot operate with the rest of the infrastructure, there is a likelihood for introducing new vulnerabilities.
For example, National Institute for Science and Technology (NIST) recently selected SHA-3 on August 5th, 2015 (Dworkin, 2017). This is the latest encryption algorithm approved by NIST. However, is your organization ready to deploy it? How will it fit with the other layers of the overall security model? How will interoperate with the existing modules? Steps will need to be taken (as defined by security procedures) to test the algorithm end-to-end. As an example, most cryptographic failures happen due to poor and incorrect implementations usually caused by configuration errors, not the algorithm itself. A recent study reported that only 17% of the cryptographic failures were caused by bugs in the cryptographic libraries by individual applications. However, 83% are misuses of cryptographic libraries by individual applications, in other words, incorrect configuration (Lazar, 2014). |
3. Multi-vendor vs Single SourceIt is recommended your organization take a best-of-breed approach utilizing multiple vendors including in-house development for specific security services. This is aligned with the first theme regarding componentized versus monolithic approach, but the emphasis is on the vendors. Further, some aspects of the security strategy should remain on-premise and within the organization and not outsourced. For example, policies should be developed and maintained in-house with a named owner within the organization. Whereas, Intrusion Detection Systems (IDS) is a play best suited for an external vendor either as a service (SaaS) or on-premise.
|