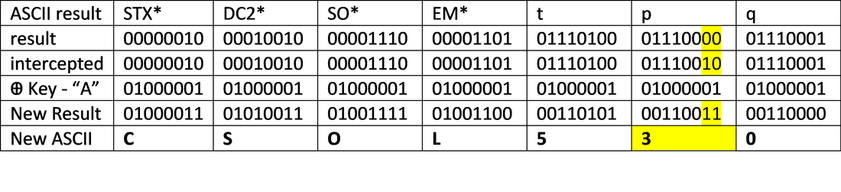Hash Functions Definition |
Major Considerations |
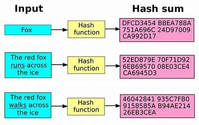
Figure 1 - Apple Example |
Does Encryption Support Data Integrity?
The simple answer is "no". Encryption by itself will not ensure data integrity. The example below will illustrate this. To see how integrity of a message is maintained, see the Message Authentication Codes (MAC's) page on this website.
In this example, I converted the text “CSOL510” to binary and then XOR’d that binary to a cipher with a repeating key using the binary equivalent of “A” (01000001). Assuming this is correct, the XOR’d cipher is below.
In this example, I converted the text “CSOL510” to binary and then XOR’d that binary to a cipher with a repeating key using the binary equivalent of “A” (01000001). Assuming this is correct, the XOR’d cipher is below.
I would argue that in this case, the plain text “CSOL510” is confidential until someone either cracks it or has the key “A” (in binary). However, there are no assurances the integrity of the message has not been compromised. In the example below, I changed one of the bits in the sixth word “1” to the binary equivalent of the number “3”.
It’s a long and drawn-out way to say that a single bit change in the encrypted message will compromise the integrity of the message without the receiver knowing it was compromised, yet it required the key to decrypt. Therefore, the confidentiality was maintained, but the integrity was not. As a result, a MAC is required to maintain the integrity of the message. If this were a real example, a student who thought she was registered for the course CSOL 510 may have received a confirmation that she is enrolled in CSOL 530.