
Risk Management - As breaches continue to grow, the risk to an organization like ours becomes a greater concern. Cyber-risk continues to climb in relative importance among all global business risks; in 2013 it was ranked 15th, in 2014 it moved to the 8th position and in 2016 it was identified as the 3rd biggest risk to an organization ahead of natural catastrophes, changes in legislation and regulations, macroeconomic developments and fraud (Allianz, 2016). As this becomes a more prominent risk factor for organizations, insurers are now underwriting cyber-breaches (e.g. information theft, business disruption, revenue loss and equipment damage) with 60 carriers now offering stand-alone cyber-insurance policies. The value of these premiums was valued at $3.25 billion in 2016 with some estimates suggesting this will quickly grow to over $7.5 billion (Hartwig & Wilkinson, 2016). However, no insurance will cover loss or damage to a reputation (Ross, 2014).
The goal of this page is to show how to ensure the system remains secure in light of changes to personnel, environment and technologies. In order to accomplish this goal, it is recommended to leverage a number of the documents published by the National Institute of Standards and Technology (NIST). Specifically, NIST Special Publication (SP) 800-53 provides a six-step framework for aligning the accepted risk profile to our IT infrastructure. The example will use a corporate payroll system to illustrate how the concepts from NIST apply to a familiar system.
The goal of this page is to show how to ensure the system remains secure in light of changes to personnel, environment and technologies. In order to accomplish this goal, it is recommended to leverage a number of the documents published by the National Institute of Standards and Technology (NIST). Specifically, NIST Special Publication (SP) 800-53 provides a six-step framework for aligning the accepted risk profile to our IT infrastructure. The example will use a corporate payroll system to illustrate how the concepts from NIST apply to a familiar system.
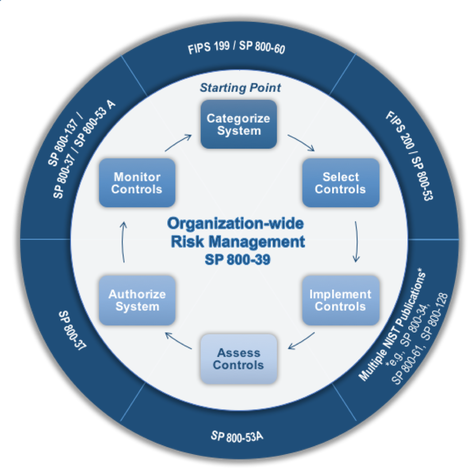
The Overall Process for Managing Risk
The risk management framework (RMF) is a six-step process that defines the level of risk a process owner is willing to accept to meet the needs of the business. This provides a disciplined and structured process that integrates information security and risk management activities into the system development life-cycle. As this system is adopted across our organization there will be a fundamental change to how we operate. First, the leadership team will have a more active role in guiding the overall risk profile of the organization. Second, the process of risk assessment will be infused in the overall IT infrastructure throughout the course of the development life-cycle. The over-arching theme is “build it right, continuously monitor” (Ross, 2014). The first five steps in the process discuss how to build the in-depth strategy to ensure there is a stable and secure system in place to support our payroll system. The final step, if performed correctly, will ensure our systems are constantly being reviewed for changes to our system whether they originate from changes in staff, systems or threats.
The risk management framework (RMF) is a six-step process that defines the level of risk a process owner is willing to accept to meet the needs of the business. This provides a disciplined and structured process that integrates information security and risk management activities into the system development life-cycle. As this system is adopted across our organization there will be a fundamental change to how we operate. First, the leadership team will have a more active role in guiding the overall risk profile of the organization. Second, the process of risk assessment will be infused in the overall IT infrastructure throughout the course of the development life-cycle. The over-arching theme is “build it right, continuously monitor” (Ross, 2014). The first five steps in the process discuss how to build the in-depth strategy to ensure there is a stable and secure system in place to support our payroll system. The final step, if performed correctly, will ensure our systems are constantly being reviewed for changes to our system whether they originate from changes in staff, systems or threats.
Categorizing Assets
Information categorization is the first step in developing a risk management framework (RMF). Categorization determines the impact level for confidentiality, integrity and availability based on the information that is being stored, transmitted and processed across systems. It determines the criticality and sensitivity of the information system according to the potential worst case, adverse impact to the business. There are four steps to categorizing assets: identifying information types, selecting provisional impact levels, reviewing and adjusting provisional impact levels and assigning system security categories.
A payroll system organizes all employee payment tasks and the filing of employee taxes (Bragg, 2003). For many organizations, this represents the single largest expense line item in our income statement. It is also our most complex reporting process as employees work in many countries not including states and provinces within countries, many of which have unique taxes and reporting requirements. Moreover, fines vary by country, states and provinces. Therefore, it is critical that organizations have the proper security controls in place to effectively mitigate risks to this data.
Selecting Controls
Based on analysis from the information categorization effort, it is determined that this payroll system is classified as a “high” impact system. Below is the recommended guideline established by FIPS publication 200 (NIST, 2006) as the format used to express it over the objectives of confidentiality, integrity and availability.
SC Payroll = {(Confidentiality, High), (Integrity, High), (Availability, High)}
organizations need to determine the best security controls to address the needs of our payroll system as defined by the level of impact--in this case a High-impact system. Table 3 – Security Control Proposal for our Payroll System illustrates the controls that were selected for our payroll system. These were obtained from NIST SP 800-53 which provides a catalogue of 20 families of pre-determined controls that were used to facilitate this process step. Some security controls reduce the likelihood of a threat occurring while others are designed to reduce the impact of an incident. Table 3 identifies the control family, baseline and control type.
There are two important points for the executive team to understand for this step. First, leveraging industry standard controls developed by the Federal Government which allows us to adopt existing best practices and save time. Second, where possible, implement common control types to leverage our existing security investments. This keeps our costs to implement and complexity to maintain the controls to a minimum.
Implementing Controls
The purpose of the implementation step is to implement the security and privacy controls that were selected in the previous step. There are two primary tasks in this step; first, implement the security controls specified in the security plan and second, thoroughly document the implementation plan for each control including the inputs, expected behavior and expected outputs (See Table 4 – Implementation of Access Controls). This level of documentation is required in order to have complete traceability of our decisions. In some cases, the implementations will be technical, while in others, they will be administrative. This is an important point for the executive leadership team as the implementation of some controls will require participation from the business.
Organizations do not have infinite resources. Therefore, they need to develop a strategy that optimizes resources while accomplishing the greatest risk reduction. The first component of the strategy is to implement controls that have the greatest benefit based on a prioritization scheme in the security controls table (See Table 3). Next, follow an engineering approach that ensures the pieces fit together to form a cohesive whole. Next, balance the security needs of the organization with the functionality and usability needs of the user community. Finally, leverage the common existing controls within our payroll system and supplement with compensating controls.
Assessing Security Controls
Control assessments are used to identify vulnerabilities in the information systems within an organization and the environment in which they operate (Ross, 2012). The assessments ensure the controls were implemented correctly. This section will provide a brief background of the assessment process, but more importantly, it will highlight a specific example of how to leverage this activity to mitigate a vulnerability in the payroll system that could have resulted in significant fines and consequences to our employees and the brand.
The assessment process is composed of four distinct steps: preparing the assessment, conducting the assessment, communicating the results and the ongoing maintenance of the assessment (Ross, 2012). Risk models help the organization determine the overall organizational risk by constructing a scenario to identify the source of the threat, the threat event, vulnerabilities, and predisposing conditions that cause an adverse impact. The model uses measures to help quantify the overall risk, they include the likelihood of initiation (source), likelihood of success (event), and the degree (harm) (See Table 5 – Payroll Risk Model). This allows the organization to prioritize remediation efforts to reduce the overall risk.
In contrast to conventional thinking, spending more money on security does not necessarily translate to a more secure system. Gartner recently published a study finding the most secure organizations sometimes spend less than the average on security as a percentage of IT budget. According to Gartner, the lowest-spending 20% of enterprises are composed of two distinctly different types of organizations (Moore, 2016):
The first step in the assessment process was to prepare for the assessment. This is a payroll system and contains Personally Identifiable Information (PII) data. Therefore, extra care was taken to remind our assessors of the data sensitivity, and each assessor was required to sign a specific Non-Disclosure Agreement (NDA).
The next step was to conduct the assessment (See Table 6 – Assessment Results for Access Controls). In this case AC-3 and AC-5 both failed. After conducting a detailed analysis to determine the root cause, we determined the system responsible for modifying an employee’s role was not configured properly when they moved within a department. For example, if an employee moved from Human Resources (HR) to Finance, the control worked as expected. However, if the employee within HR moved from the compensation committee (sub-dept) to recruiting, they still maintained create/read/edit/delete (CRED) access to compensation. This was also true for movement to other geographic regions within HR. We learned this was an unintentional error. Our analysis revealed that we established a new structure to the HR organization at the beginning of the year that creates a separate entity within HR, a compensation committee. This department within HR is newly formed, unfortunately the business applications systems were not reconfigured to support the new access controls that would be required.
This is an example of how a simple change to employees’ movement within the organization caused an impact to the threat surface and to our controls that were already in place. Had we not taken a structured and detailed approach to proactively assess our controls, it is highly unlikely this would have been discovered before an accidental discovery or a serious incident would have occurred. We have since remediated this risk and updated our processes to prevent this from occurring in the future.
Authorizing Information Systems
This is the step where the Authorization Official (AO) is responsible for making the final decision on whether the system can operate, operate with conditions, or not operate. This section summarizes key elements defined in a formal authorization package which consists of an executive summary, security and privacy plans, assessment reports and plans of action and milestones (POA&M) (Ross & Swanson, 2002).
The overall risk to our payroll system is measured across three categories: adversarial, accidental and environmental. Our team identified six primary threat scenarios with two that were determined to have a risk profile of ‘High” and “Very High” for the payroll system. The high-risk scenario is related to a potentially disgruntled employee with elevated permissions. The very high-risk scenario is the threat scenario related to a negligent employee with elevated privileges who does not perform a necessary patch to our payroll system. The key difference being the likelihood of the event happening. It is believed that an accident is more likely to occur than a malicious threat executed from the inside.
The risk profile illustrates a very high overall risk to the organization that we believe can be remediated with a minimal level of effort and investment within a relatively short period of time (e.g., two weeks) (See Table 5 – Payroll Risk Model). The next step in this example would be a recommended action to the AO; in this example it would be to continue to operate with conditions.
The analogy to this process is how we as a software company make the decision to launch a new product or Route-to-Customer (RTC). Multiple stakeholders from development, quality, support and industry teams must all be in agreement prior to RTC. We will adopt the same methodology for authorizing our Information Systems in order to provide a defense in-depth security model.
Continuous Monitoring
Regrettably, IT infrastructures are not made of plastic. If it were, we would be done at the authorizing step. Because our environment is dynamic, new employees, new software and hardware and new threat vectors are occurring in near real-time. Therefore, we need a process for re-evaluating our infrastructure for vulnerabilities. This requires good situational awareness, which is knowing where our systems are at any point in time. Security controls will need to be assessed and analyzed at a frequency that is sufficient to support the desired risk to protect information established by the executive team.
There are three core functions of a good continuous monitoring process: determine the effectiveness of the controls that have been implemented, respond to any perturbation to the IT infrastructure (employees, technology, processes) and verify any compliance issues to legislation, directives, policies or standards. We will employ the following steps to implement our continuous monitoring process:
Information categorization is the first step in developing a risk management framework (RMF). Categorization determines the impact level for confidentiality, integrity and availability based on the information that is being stored, transmitted and processed across systems. It determines the criticality and sensitivity of the information system according to the potential worst case, adverse impact to the business. There are four steps to categorizing assets: identifying information types, selecting provisional impact levels, reviewing and adjusting provisional impact levels and assigning system security categories.
A payroll system organizes all employee payment tasks and the filing of employee taxes (Bragg, 2003). For many organizations, this represents the single largest expense line item in our income statement. It is also our most complex reporting process as employees work in many countries not including states and provinces within countries, many of which have unique taxes and reporting requirements. Moreover, fines vary by country, states and provinces. Therefore, it is critical that organizations have the proper security controls in place to effectively mitigate risks to this data.
Selecting Controls
Based on analysis from the information categorization effort, it is determined that this payroll system is classified as a “high” impact system. Below is the recommended guideline established by FIPS publication 200 (NIST, 2006) as the format used to express it over the objectives of confidentiality, integrity and availability.
SC Payroll = {(Confidentiality, High), (Integrity, High), (Availability, High)}
organizations need to determine the best security controls to address the needs of our payroll system as defined by the level of impact--in this case a High-impact system. Table 3 – Security Control Proposal for our Payroll System illustrates the controls that were selected for our payroll system. These were obtained from NIST SP 800-53 which provides a catalogue of 20 families of pre-determined controls that were used to facilitate this process step. Some security controls reduce the likelihood of a threat occurring while others are designed to reduce the impact of an incident. Table 3 identifies the control family, baseline and control type.
There are two important points for the executive team to understand for this step. First, leveraging industry standard controls developed by the Federal Government which allows us to adopt existing best practices and save time. Second, where possible, implement common control types to leverage our existing security investments. This keeps our costs to implement and complexity to maintain the controls to a minimum.
Implementing Controls
The purpose of the implementation step is to implement the security and privacy controls that were selected in the previous step. There are two primary tasks in this step; first, implement the security controls specified in the security plan and second, thoroughly document the implementation plan for each control including the inputs, expected behavior and expected outputs (See Table 4 – Implementation of Access Controls). This level of documentation is required in order to have complete traceability of our decisions. In some cases, the implementations will be technical, while in others, they will be administrative. This is an important point for the executive leadership team as the implementation of some controls will require participation from the business.
Organizations do not have infinite resources. Therefore, they need to develop a strategy that optimizes resources while accomplishing the greatest risk reduction. The first component of the strategy is to implement controls that have the greatest benefit based on a prioritization scheme in the security controls table (See Table 3). Next, follow an engineering approach that ensures the pieces fit together to form a cohesive whole. Next, balance the security needs of the organization with the functionality and usability needs of the user community. Finally, leverage the common existing controls within our payroll system and supplement with compensating controls.
Assessing Security Controls
Control assessments are used to identify vulnerabilities in the information systems within an organization and the environment in which they operate (Ross, 2012). The assessments ensure the controls were implemented correctly. This section will provide a brief background of the assessment process, but more importantly, it will highlight a specific example of how to leverage this activity to mitigate a vulnerability in the payroll system that could have resulted in significant fines and consequences to our employees and the brand.
The assessment process is composed of four distinct steps: preparing the assessment, conducting the assessment, communicating the results and the ongoing maintenance of the assessment (Ross, 2012). Risk models help the organization determine the overall organizational risk by constructing a scenario to identify the source of the threat, the threat event, vulnerabilities, and predisposing conditions that cause an adverse impact. The model uses measures to help quantify the overall risk, they include the likelihood of initiation (source), likelihood of success (event), and the degree (harm) (See Table 5 – Payroll Risk Model). This allows the organization to prioritize remediation efforts to reduce the overall risk.
In contrast to conventional thinking, spending more money on security does not necessarily translate to a more secure system. Gartner recently published a study finding the most secure organizations sometimes spend less than the average on security as a percentage of IT budget. According to Gartner, the lowest-spending 20% of enterprises are composed of two distinctly different types of organizations (Moore, 2016):
- Unsecure organizations that underspend; and
- Secure organizations that have reduced the overall complexity of the IT infrastructure and, as a result, have reduced the number of security vulnerabilities through implementation of IT and security best practices.
The first step in the assessment process was to prepare for the assessment. This is a payroll system and contains Personally Identifiable Information (PII) data. Therefore, extra care was taken to remind our assessors of the data sensitivity, and each assessor was required to sign a specific Non-Disclosure Agreement (NDA).
The next step was to conduct the assessment (See Table 6 – Assessment Results for Access Controls). In this case AC-3 and AC-5 both failed. After conducting a detailed analysis to determine the root cause, we determined the system responsible for modifying an employee’s role was not configured properly when they moved within a department. For example, if an employee moved from Human Resources (HR) to Finance, the control worked as expected. However, if the employee within HR moved from the compensation committee (sub-dept) to recruiting, they still maintained create/read/edit/delete (CRED) access to compensation. This was also true for movement to other geographic regions within HR. We learned this was an unintentional error. Our analysis revealed that we established a new structure to the HR organization at the beginning of the year that creates a separate entity within HR, a compensation committee. This department within HR is newly formed, unfortunately the business applications systems were not reconfigured to support the new access controls that would be required.
This is an example of how a simple change to employees’ movement within the organization caused an impact to the threat surface and to our controls that were already in place. Had we not taken a structured and detailed approach to proactively assess our controls, it is highly unlikely this would have been discovered before an accidental discovery or a serious incident would have occurred. We have since remediated this risk and updated our processes to prevent this from occurring in the future.
Authorizing Information Systems
This is the step where the Authorization Official (AO) is responsible for making the final decision on whether the system can operate, operate with conditions, or not operate. This section summarizes key elements defined in a formal authorization package which consists of an executive summary, security and privacy plans, assessment reports and plans of action and milestones (POA&M) (Ross & Swanson, 2002).
The overall risk to our payroll system is measured across three categories: adversarial, accidental and environmental. Our team identified six primary threat scenarios with two that were determined to have a risk profile of ‘High” and “Very High” for the payroll system. The high-risk scenario is related to a potentially disgruntled employee with elevated permissions. The very high-risk scenario is the threat scenario related to a negligent employee with elevated privileges who does not perform a necessary patch to our payroll system. The key difference being the likelihood of the event happening. It is believed that an accident is more likely to occur than a malicious threat executed from the inside.
The risk profile illustrates a very high overall risk to the organization that we believe can be remediated with a minimal level of effort and investment within a relatively short period of time (e.g., two weeks) (See Table 5 – Payroll Risk Model). The next step in this example would be a recommended action to the AO; in this example it would be to continue to operate with conditions.
The analogy to this process is how we as a software company make the decision to launch a new product or Route-to-Customer (RTC). Multiple stakeholders from development, quality, support and industry teams must all be in agreement prior to RTC. We will adopt the same methodology for authorizing our Information Systems in order to provide a defense in-depth security model.
Continuous Monitoring
Regrettably, IT infrastructures are not made of plastic. If it were, we would be done at the authorizing step. Because our environment is dynamic, new employees, new software and hardware and new threat vectors are occurring in near real-time. Therefore, we need a process for re-evaluating our infrastructure for vulnerabilities. This requires good situational awareness, which is knowing where our systems are at any point in time. Security controls will need to be assessed and analyzed at a frequency that is sufficient to support the desired risk to protect information established by the executive team.
There are three core functions of a good continuous monitoring process: determine the effectiveness of the controls that have been implemented, respond to any perturbation to the IT infrastructure (employees, technology, processes) and verify any compliance issues to legislation, directives, policies or standards. We will employ the following steps to implement our continuous monitoring process:
- determine the security impact of the proposed or actual changes to the system;
- assess the security controls based on the monitoring strategy; and
- conduct remediation based on the results of the monitoring, assessment of risk and items in the POA&M.
References
Allianz Global Corporate, Inc. (2016). Allianz Risk Barometer 2016. Retrieved March 10, 2018, from http://www.agcs.allianz.com/insights/white-papers-and-case-studies/allianz-risk-barometer-2016/
Bragg, S. M. (2003). Essentials of payroll: management and accounting. New York: John Wiley and Sons Ltd.
Hartwig, R., PhD., & Wilkinson, C. (2016, October 27). Cyberrisk: Threat and opportunity. Retrieved March 10, 2018, from https://www.iii.org/white-paper/cyberrisk-threat-and-opportunity-102716
Information Technology Laboratory (National Institute of Standards and Technology).,
Computer Security Division. (2006). Minimum security requirements for federal information and information systems FIPS PUB 200. Gaithersburg, MD: National Institute of Standards and Technology.
Moore, S. (2016, December 9). Gartner Says Many Organizations Falsely Equate IT Security Spending with Maturity. Retrieved February 25, 2018, from https://www.gartner.com/newsroom/id/3539117
Ross, R. (2014). Guide for assessing the security controls in federal information systems: building effective security assessment plans (NIST Special Publication 800-53 r5). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
Ross, Ron. “The Fundamentals of Continuous Monitoring – An Integral Part of Risk Management Strategies” Online video clip. YouTube. YouTube, 2014, June 09. Retrieved March 09, 2018
Ross, R. (2012). Guide for conducting risk assessments (NIST Special Publication 800-30 r1). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
Ross, R., & Swanson, M. (2002). Guidelines for the security certification and accreditation of federal information technology systems (NIST Special Publication 800-37 r2). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
Allianz Global Corporate, Inc. (2016). Allianz Risk Barometer 2016. Retrieved March 10, 2018, from http://www.agcs.allianz.com/insights/white-papers-and-case-studies/allianz-risk-barometer-2016/
Bragg, S. M. (2003). Essentials of payroll: management and accounting. New York: John Wiley and Sons Ltd.
Hartwig, R., PhD., & Wilkinson, C. (2016, October 27). Cyberrisk: Threat and opportunity. Retrieved March 10, 2018, from https://www.iii.org/white-paper/cyberrisk-threat-and-opportunity-102716
Information Technology Laboratory (National Institute of Standards and Technology).,
Computer Security Division. (2006). Minimum security requirements for federal information and information systems FIPS PUB 200. Gaithersburg, MD: National Institute of Standards and Technology.
Moore, S. (2016, December 9). Gartner Says Many Organizations Falsely Equate IT Security Spending with Maturity. Retrieved February 25, 2018, from https://www.gartner.com/newsroom/id/3539117
Ross, R. (2014). Guide for assessing the security controls in federal information systems: building effective security assessment plans (NIST Special Publication 800-53 r5). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
Ross, Ron. “The Fundamentals of Continuous Monitoring – An Integral Part of Risk Management Strategies” Online video clip. YouTube. YouTube, 2014, June 09. Retrieved March 09, 2018
Ross, R. (2012). Guide for conducting risk assessments (NIST Special Publication 800-30 r1). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
Ross, R., & Swanson, M. (2002). Guidelines for the security certification and accreditation of federal information technology systems (NIST Special Publication 800-37 r2). Gaithersburg, MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.