Vulnerability Detection |
|

The objective is to choose a free, open source vulnerability management tool to discover, identify, categorize, and assess vulnerabilities for all assets in a networked environment including network devices, operating systems, and applications. Must be able to reveal vulnerabilities that need to be tracked and/or fixed and patched based on their risk. The tool needs to contain the following four components (Singh, 2016):
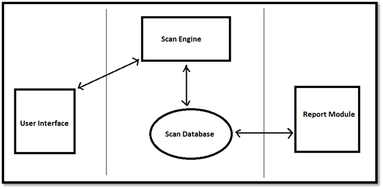
- User Interface - either a graphical UI (GUI) or a command line interface (CLI)
- Scan Engine - scan execution leveraging a database of known vulnerabilities
- Scan Database – dbase of known vulnerabilities the scan engine leverages
- Reporting framework – captures the detailed scan results in a human readable format
Some of the core features that are required for the Vulnerability assessment tool are: (table stakes)
- Maintain an updated database for latest vulnerabilities.
- Ability to detect vulnerabilities with less false positives.
- Ability to scan multiple targets simultaneously.
- Ability to provide a detailed report with vulnerable request and response pair.
- Provides recommendations to fix the vulnerabilities.
- Ability to scan for both external and internal vulnerabilities.
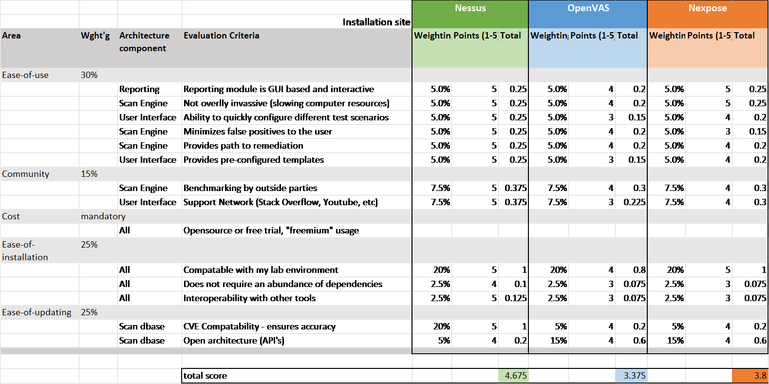
Criteria that will be used for the selection include:
- Ease-of-use – The tool must provide a graphical user interface and specifically in the reporting module.
- Cost – For purposes of this assignment, the tool must be available for download for use in a limited environment, like my lab for example.
- Ease of Installation – Given the limited time to conduct the analysis, this must be easily installed by someone with limited Linux skills. This will be assessed by length of time based on known hassle and frustration factor.
- Ease-of-updating – vulnerability scanners need to be current with the latest vulnerability dbase.
- Community – Ability to get fast answers to common problems and questions will be very important for meeting the deadline of this assignment.
I decided to use take the RFP approach to selecting a tool. This was done to ensure that I remained objective in my evaluation versus getting lured into the tool with the coolest looking graphics and UI. I built my RFP with the five criteria described above and used a weighted average scoring method.
Below is a summary of the evaluation across the vendors:
|
Product |
Background |
Overall Score |
|
Nessus |
Nessus is a proprietary vulnerability scanner developed by
Tenable Network Security. It is free of charge for personal use in a
non-enterprise environment. According to surveys done in 2009 by
sectools.org, Nessus is the world's most popular vulnerability scanner,
taking first place in the 2000, 2003, and 2006 security tools survey. Tenable
Network Security estimated in 2005 that it was used by over 75,000
organizations worldwide. |
4.65 |
|
OpenVAS |
OpenVAS (Open Vulnerability Assessment System, originally known
as GNessUs) is a software framework of several
services and tools offering vulnerability scanning and vulnerability
management. All OpenVAS products are free software, and most components are
licensed under the GNU General Public License (GPL). Plugins for OpenVAS are
written in the Nessus Attack Scripting Language, NASL. |
3.40 |
|
Nexpose |
Nexpose is a vulnerability scanner which aims to support the
entire vulnerability management lifecycle, including discovery, detection,
verification, risk classification, impact analysis, reporting and mitigation.
It integrates with Rapid7's Metasploit for vulnerability exploitation. |
3.80 |
|
Steps |
Commands |
Results |
|
Go to Tenable.com and obtain activation code |
https://www.tenable.com/downloads/nessus |
|
|
Fill-out mandatory form, check email for activation code |
Enter first, last and email |
Activating Your Nessus
Home Subscription
Your
activation code for Nessus Home is: |
|
Locate current Debian version |
root@kali: uname -a |
Linux kali 4.17.0-kali1-amd64 #1 SMP Debian 4.17.8-1kali1
(2018-07-24) x86_64 GNU/Linux |
|
Download the correct version |
|
Once the download is complete, check the “Downloads” folder. You should see this: |
|
Open the command window and look for the downloaded file |
root@kali: cd Downloads root@kali:~/Downloads# la -lah |
drwxr-xr-x
2 root root 4.0K Aug 4 14:39 . drwxr-xr-x 17 root root 4.0K Aug 4 14:04 .. -rw-r--r-- 1 root root 62M Aug
4 14:39 Nessus-7.1.3-debian6_amd64.deb |
|
Install Nessus |
root@kali:~/Downloads# dpkg -i Nessus-7.1.3-debian6_amd64.deb Nessus-7.1.3-debian6_amd64.deb
|
Selecting previously unselected package nessus. (Reading database ... 347632 files and directories
currently installed.) Preparing to unpack Nessus-7.1.3-debian6_amd64.deb ... Unpacking nessus (7.1.3) ... Preparing to unpack Nessus-7.1.3-debian6_amd64.deb ... Shutting down Nessus : . Unpacking nessus (7.1.3) over (7.1.3) ... More than one copy of package nessus has been unpacked in this run ! Only
configuring it once. Setting up nessus (7.1.3) ... Unpacking Nessus Core Components... - You can start Nessus by
typing /etc/init.d/nessusd start - Then go to
https://kali:8834/ to configure your scanner Processing triggers for systemd
(239-7)
... |
|
Launch Nessus |
root@kali
/etc/init.d/nessusd
start |
root@kali:~/Downloads# /etc/… Starting Nessus : root@kali:~/Downloads# |
|
Open a browser and sign-in to access Nessus |
https://kali:8834/ |
|
|
View the home page of Nessus |
|
|
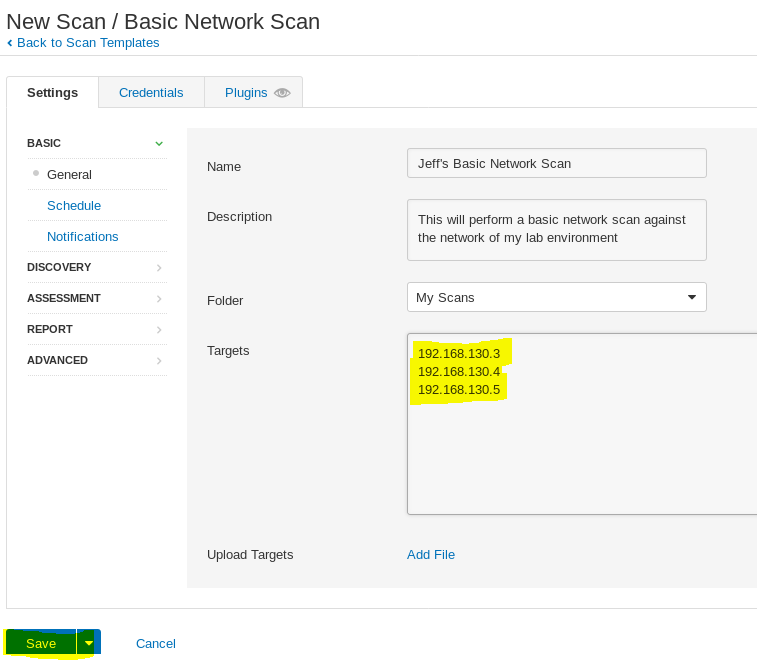
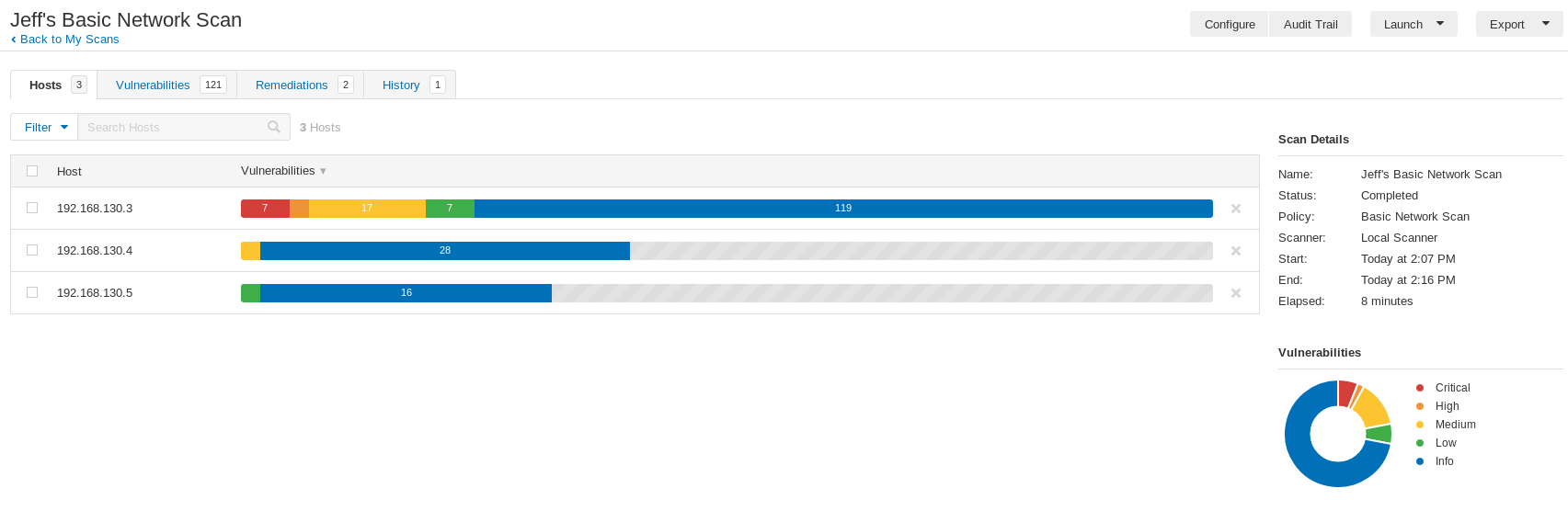
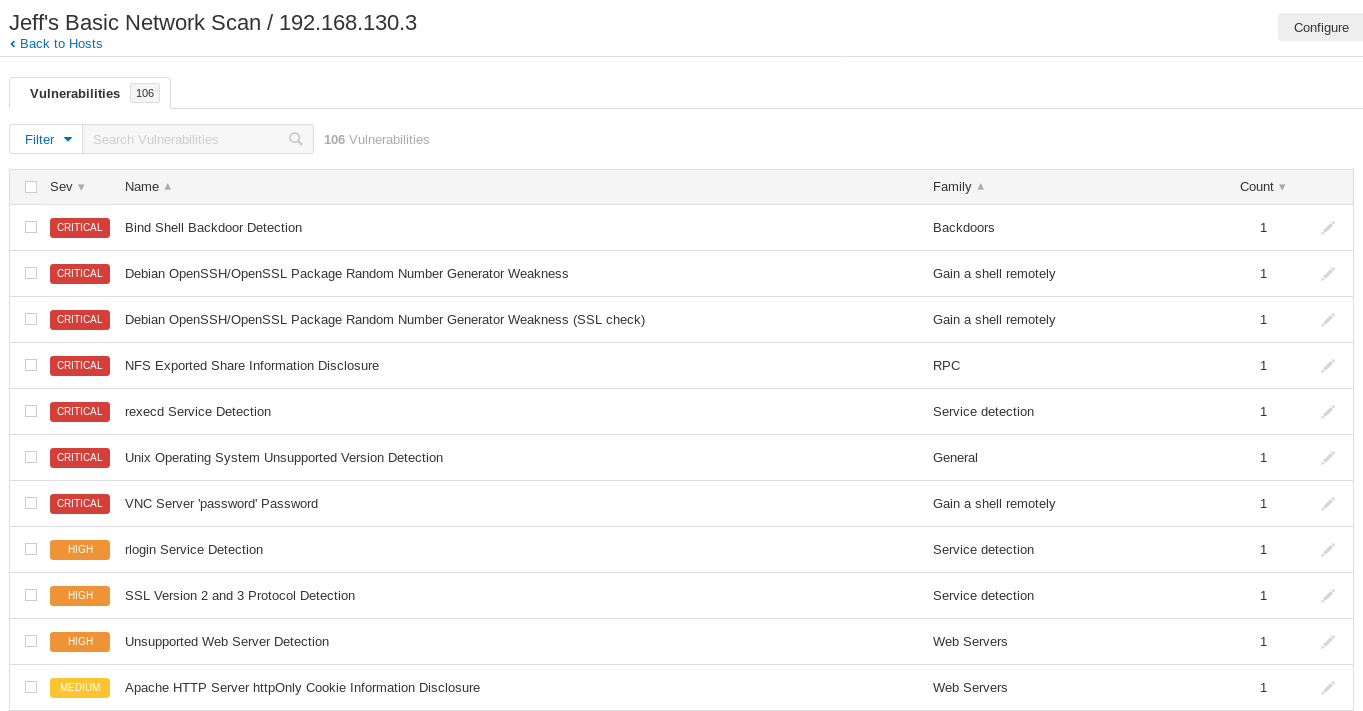
Once the software completed the installation process, I created a test scenario, ran the scan and analyzed the output found in the reports.
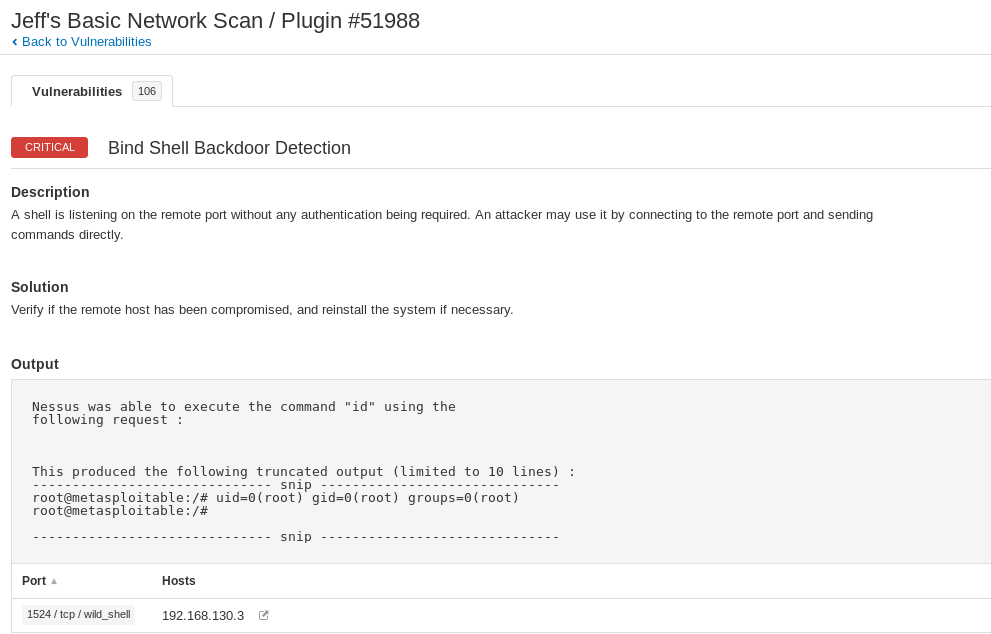
I conducted some research and found the vulnerability that Nessus identified. Ingreslock is a service that is used to legitimately lock parts of the Ingres dbase. However, there are known trojans that also use port 1524 as a backdoor into a system. Some system admins allow this port to be open thinking it is needed. The recommended remediation by Nessus is to simply close the port. I did some further research to figure out how I could do this. My intention was to close the port and then re-run the Nessus scan. My hypothesis was that the vulnerability would disappear. After several attempts and many searches, I found some Linux commands that should have worked. Unfortunately, I was unsuccessful. My next attempt will be to close the port on the firewall to the node. This will require additional research and of course time.
HackerTarget. (2018, March 07). Nessus, OpenVAS and Nexpose VS Metasploitable. Retrieved
August 5, 2018, from https://hackertarget.com/nessus-openvas-nexpose-vs-metasploitable/
OWASP. (2018, August 9). Category:Vulnerability Scanning Tools. Retrieved August 10, 2018, from https://www.owasp.org/index.php/Category:Vulnerability_Scanning_Tools
Tittle, E. (2016, February). Comparing the top vulnerability management tools. Retrieved August
6, 2018, from https://searchsecurity.techtarget.com/feature/Comparing-the-top-vulnerability-management-tools
RWB Network Security. (n.d.). Penetration Testing Tutorials for the Beginner. Retrieved August
6, 2018, from http://www.rwbnetsec.com/ingreslock/
Singh, S. (2016, July 10). Vulnerability Scanners. Retrieved August 5, 2018, from
https://resources.infosecinstitute.com/vulnerability-scanners-2/#gref