Return on Investment (ROI) of Cyber Security

Executive Summary
This section will discuss the tools that are used to generate an investment proposal; Financial Services Sector Coordinating Council Automated Cybersecurity Assessment Tool (FSSCC ACAT) and the Information Technology Return on Investment Tool (IT Initiative ROI Tool). When used together, they form the ability to create an overall business case to justify investments in cybersecurity initiatives. The FSSCC sheet provides guidance on where to invest, the ROI tool provides guidance on the economic value of the investment. Both have a place in developing the overall business case. A fictitious government agency will be used as an example.
This section will discuss the tools that are used to generate an investment proposal; Financial Services Sector Coordinating Council Automated Cybersecurity Assessment Tool (FSSCC ACAT) and the Information Technology Return on Investment Tool (IT Initiative ROI Tool). When used together, they form the ability to create an overall business case to justify investments in cybersecurity initiatives. The FSSCC sheet provides guidance on where to invest, the ROI tool provides guidance on the economic value of the investment. Both have a place in developing the overall business case. A fictitious government agency will be used as an example.
Supporting Tool #1 – The FSSCC Calculator to Determine Risk
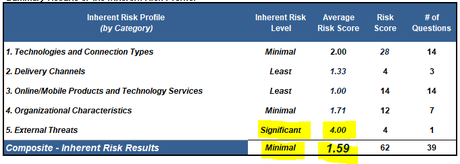
The FSSCC calculator was developed in 2015 by the Federal Financial Institutions Examination Council (FFIEC) for the purpose of assisting financial institutions in determining their risks and the maturity of their cybersecurity programs. Although originally developed for financial institutions, this still has applicability for government agencies. The calculator consists of two main components; the inherent risk modeler and the maturity assessment tool. Across both components, the calculator follows three steps; first, the organization must identify and review the inherent risks. Next, management can make a determination as to whether the maturity levels are appropriate for the level of risk and finally, management can either chose to reduce the level of risk or increase the levels of maturity as appropriate (NCAUChannel, 2015). Based on sample inputs provided in the risk modeler, this federal agency has an overall risk score of 1.59 which is determined to be minimal (See Figure 1 – Summary Results of the
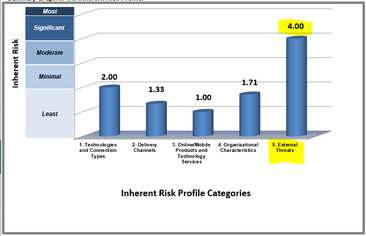
Inherent Risk Profile). However, this is the arithmetic mean across five categories; technologies and connection types, delivery channels, online/mobile products, organizational characteristics and finally external threats. Although the overall risk assessment is determined to be “minimal”, there exists a “significant” risk for the category of external threats. See figure 2 – Summary graph of Inherent Risk Profile below:
The FSSCC calculator was developed in 2015 by the Federal Financial Institutions Examination Council (FFIEC) for the purpose of assisting financial institutions in determining their risks and the maturity of their cybersecurity programs. Although originally developed for financial institutions, this still has applicability for government agencies. The calculator consists of two main components; the inherent risk modeler and the maturity assessment tool. Across both components, the calculator follows three steps; first, the organization must identify and review the inherent risks. Next, management can make a determination as to whether the maturity levels are appropriate for the level of risk and finally, management can either chose to reduce the level of risk or increase the levels of maturity as appropriate (NCAUChannel, 2015). Based on sample inputs provided in the risk modeler, this federal agency has an overall risk score of 1.59 which is determined to be minimal (See Figure 1 – Summary Results of the
Inherent Risk Profile). However, this is the arithmetic mean across five categories; technologies and connection types, delivery channels, online/mobile products, organizational characteristics and finally external threats. Although the overall risk assessment is determined to be “minimal”, there exists a “significant” risk for the category of external threats. See figure 2 – Summary graph of Inherent Risk Profile below:
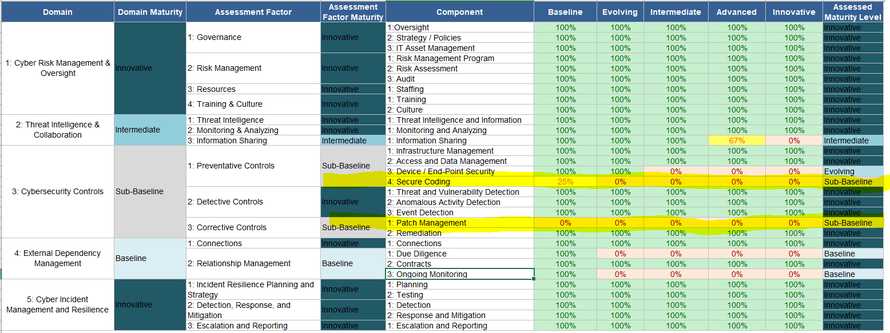
The maturity assessment tool within the calculator determines cyber preparedness across five domains; cyber risk management and oversight, threat intelligence and collaboration, cybersecurity controls, external dependency management and cyber incident management and resilience. Each domain contains assessment factors and each assessment factor contains specific components. The tool models at the component level of the taxonomy. The maturity results for this government agency highlights three domains, two that are rated as “sub-baseline” and a third domain, external dependency management is rated as “baseline” (See figure 3 – Maturity Results below).
Figure 3 - Maturity Results
Secure coding is a vulnerability that is susceptible to a well-known attack called “SQL Injections” (Pr. See-qual Injection). This form of attack is on the application, wherein the attacker can execute malicious SQL statements that control a web application’s dbase server. Regrettably this is a major vulnerability that is common across all government agencies. A recent report found that U.S. Government agencies have the least secure applications of all industry sectors; 32% have this vulnerability (Higgins, 2018). Recent government agencies to be hit by SQL injection attacks include; Oklahoma State Department of Education, District Columbia Office of the Chief Financial Officer, and the US Department of Housing and Urban Development (Zorz, 2017). All were attacks that led to successful confidential data theft.
Immature patch management programs leave organizations vulnerable to a wide range of vulnerabilities. One of the most notable and recent cases involving poor patch management was the Equifax breach in 2017 that exposed 143 million people's Social Security numbers, credit cards, driver's license numbers and other private information (Rickard, D., 2017).
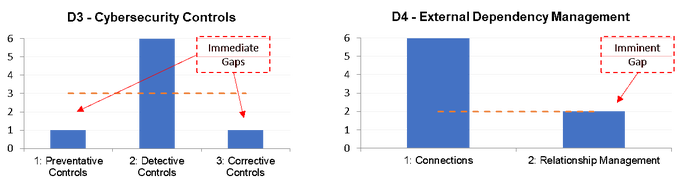
As with the private sector, government agencies are moving much of their IT infrastructure to the cloud. This poses a number of new risks that have not been addressed with the current cyber defense programs. This government agency is expected to move more operations to the cloud and specifically to Infrastructure-as-a-Service (IaaS) providers. This will require safeguards in areas like; external connections and relationship management with vendors. The government agency currently has a baseline rating for this domain, however, this will likely fall to a sub-baseline rating within the next twelve to eighteen months as the additional demands of more vendors with complexity stress the security measures. Although, this is currently not an imperative and viewed as a “nice to have”, a minor investment in this area to begin the initial work will prevent a lag in maturity. Figure 4 – Illustrates the immediate and projected areas for investment.
Immature patch management programs leave organizations vulnerable to a wide range of vulnerabilities. One of the most notable and recent cases involving poor patch management was the Equifax breach in 2017 that exposed 143 million people's Social Security numbers, credit cards, driver's license numbers and other private information (Rickard, D., 2017).
As with the private sector, government agencies are moving much of their IT infrastructure to the cloud. This poses a number of new risks that have not been addressed with the current cyber defense programs. This government agency is expected to move more operations to the cloud and specifically to Infrastructure-as-a-Service (IaaS) providers. This will require safeguards in areas like; external connections and relationship management with vendors. The government agency currently has a baseline rating for this domain, however, this will likely fall to a sub-baseline rating within the next twelve to eighteen months as the additional demands of more vendors with complexity stress the security measures. Although, this is currently not an imperative and viewed as a “nice to have”, a minor investment in this area to begin the initial work will prevent a lag in maturity. Figure 4 – Illustrates the immediate and projected areas for investment.
Figure 4 - Projected Investment Areas
Cybersecurity controls domain D3 contains three control assessments; investments are proposed for one each of preventative controls (secure coding) and corrective controls (patch management). Additional funding is being sought for external dependency management domain D4; specifically, relationship management with 3rd party cloud vendors. This will fund an investigation of processes associated with vendor monitoring and overall due diligence.
Supporting Tool #2 – IT Initiative ROI tool to Determine the Value of the Investment
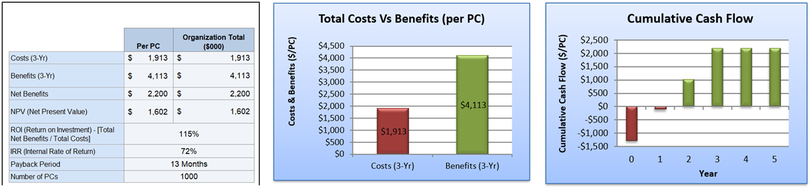
Two quantifiable ROI calculations are presented for this investment; secure coding and patch management, the third investment area is based on a qualitative factor that is included in the proposal. The first investment is for secure coding to protect the agency from SQL injection attacks. This will be a three-part investment strategy; implement a web application firewall (WAF), retrofit code to enable protection mechanisms (parameterized queries, white-list inputs and stored procedures) and re-establish least privilege rules for all dbase users (OWASP, 2016). The primary cost drivers will be additional hardware (WAF), consultants and testing software. The areas of improvement will come from increased productivity of IT applications staff and reduced down-time. Moreover, this investment will reduce overall risk profile of the agency. The ROI for this initiative is 115% with a payback period of 13 months. See figure 5 for the investment analysis. The analysis summarizes the ROI, costs versus benefits and cumulative cash flow.
Two quantifiable ROI calculations are presented for this investment; secure coding and patch management, the third investment area is based on a qualitative factor that is included in the proposal. The first investment is for secure coding to protect the agency from SQL injection attacks. This will be a three-part investment strategy; implement a web application firewall (WAF), retrofit code to enable protection mechanisms (parameterized queries, white-list inputs and stored procedures) and re-establish least privilege rules for all dbase users (OWASP, 2016). The primary cost drivers will be additional hardware (WAF), consultants and testing software. The areas of improvement will come from increased productivity of IT applications staff and reduced down-time. Moreover, this investment will reduce overall risk profile of the agency. The ROI for this initiative is 115% with a payback period of 13 months. See figure 5 for the investment analysis. The analysis summarizes the ROI, costs versus benefits and cumulative cash flow.
Figure 5 - Investment Analysis for Secure Coding
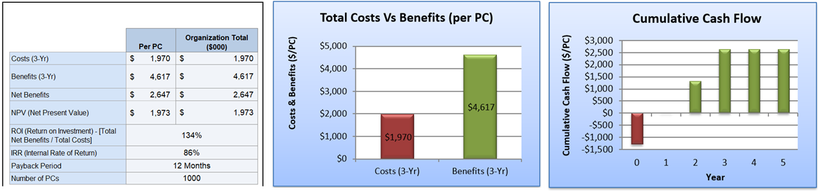
The second investment addresses the risk of vulnerability exploitation on a PC with an outdated operating system or a server with outdated components. The strategy will be to remove the human dependency from the upgrades through automated patch management. The upgrades will be mandated and controlled centrally. In the event a PC evades the automatic upgrade process, the system will apprehend control of a dangerously outdated PC or server before it can connect to the network, resulting in a company-wide outage. The primary cost drivers to this investment will be a one-time labor cost to upgrade the infrastructure and new software. Benefits will be derived from reduced service requests for the help-desk and employee downtime. Additional benefits will come from the reduced risk of malware infecting the agency network causing catastrophic downtime, disruption to business continuity and theft of agency information assets. Figure 6 provides an analysis of this investment. This investment will yield a 134% ROI with a payback of 12 months.
Figure 6 - Investment Analysis for Patch Management
The third investment seeks to fund an investigation of the agency’s strategy to migrate more of the operational IT landscape to the cloud. The current risk assessment identified the maturity of this capability to be “baseline”. However, as the migration towards the cloud and external IaaS vendors continues, there is a strong likelihood the maturity score will drop to “sub-baseline”. The estimated cost of this investment is $10,000. The primary benefit will come from overall preparedness to the cloud without increasing our risk profile. The current ROI tool is not suited for determining investments with no anticipated return. However, this investment will be far lower than the cost to react which based on internal and external discussions with leaders in the industry who were late in adopting security measures for the cloud spent three to five times the cost of this investment in recovery. Therefore, this investment is included in the proposal on its own merit as purely an investigation and the return is a qualitative ROI estimate of 200% over one year.
Conclusion
As outlined by the FSSCC assessment and validation by numerous attacks on government agencies in similar size, this agency is at risk to external threats and is not at the maturity level required for several components in the cyber defense system. Moreover, the return on investment on the secure coding project and the PC and server project justify this investment as both have ROI values higher than the agency average. In this example, it is the recommendation of the security team, based on analysis completed, to move forward immediately with these investments and fund the investigation project for the risks associated with the migration strategy to the cloud.
When working together, both tools provide a quantitative ROI for prioritizing cyber security initiatives based on a defined risk profile.
As outlined by the FSSCC assessment and validation by numerous attacks on government agencies in similar size, this agency is at risk to external threats and is not at the maturity level required for several components in the cyber defense system. Moreover, the return on investment on the secure coding project and the PC and server project justify this investment as both have ROI values higher than the agency average. In this example, it is the recommendation of the security team, based on analysis completed, to move forward immediately with these investments and fund the investigation project for the risks associated with the migration strategy to the cloud.
When working together, both tools provide a quantitative ROI for prioritizing cyber security initiatives based on a defined risk profile.