Executive Summary
Many cyber security infrastructures at discrete manufacturers are not equipped to address new threat scenarios as experienced by peer groups. There are three competing forces that are expanding the size of the attack surface and creating opportunities for a significant breach. The first is the goal for many to move many of their business applications to the cloud even though the current status is purely on-premise. As enterprises move to the cloud they will be relying on 3rd party vendors and in many cases their vendors (data centers) to host and manage confidential business data. The second force is the shifting portfolio strategy. Many are moving into the IoT space by offering their customers products that are connected. This is a strategy employed by many of their competitors, partners and customers to become closer to their customers. The third and final force is the new threat actors; the methods they use, their motivations and their resources are creating catastrophic disruptions to businesses in the industry. In combination, these three forces compel many to renovate their cyber security infrastructure.
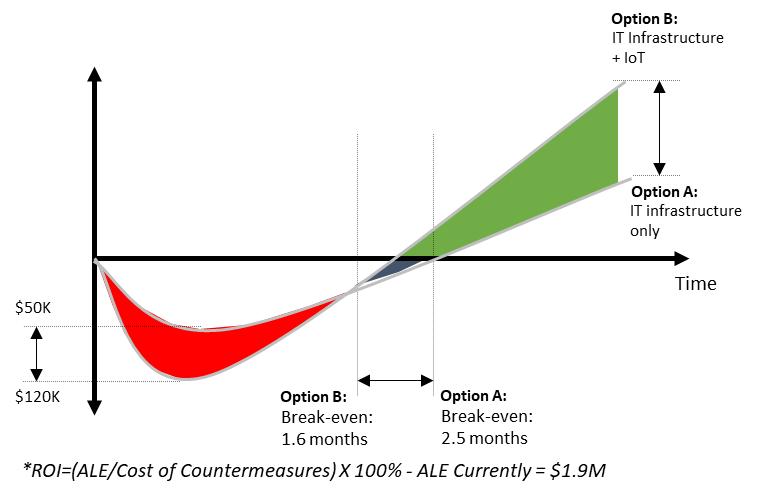
This paper, along with the accompanying PowerPoint presentation, will outline the why, what, who and how of a Cyber Threat Intelligence Plan (CTIP) for an enterprise in the discrete industries sector. The overall business case examined includes two options. Option A addresses the first force of migrating towards a hybrid landscape for business applications. Option B addresses both forces of migrating business applications to the cloud and investing in developing “cyber safe” IoT products. These options have a positive Return on Investment (RoI) of 2.5 months and 1.6 months respectively (See figure 1), placing both in the top 5 best returns a company when compared to all proposals currently in queue.
Many cyber security infrastructures at discrete manufacturers are not equipped to address new threat scenarios as experienced by peer groups. There are three competing forces that are expanding the size of the attack surface and creating opportunities for a significant breach. The first is the goal for many to move many of their business applications to the cloud even though the current status is purely on-premise. As enterprises move to the cloud they will be relying on 3rd party vendors and in many cases their vendors (data centers) to host and manage confidential business data. The second force is the shifting portfolio strategy. Many are moving into the IoT space by offering their customers products that are connected. This is a strategy employed by many of their competitors, partners and customers to become closer to their customers. The third and final force is the new threat actors; the methods they use, their motivations and their resources are creating catastrophic disruptions to businesses in the industry. In combination, these three forces compel many to renovate their cyber security infrastructure.
This paper, along with the accompanying PowerPoint presentation, will outline the why, what, who and how of a Cyber Threat Intelligence Plan (CTIP) for an enterprise in the discrete industries sector. The overall business case examined includes two options. Option A addresses the first force of migrating towards a hybrid landscape for business applications. Option B addresses both forces of migrating business applications to the cloud and investing in developing “cyber safe” IoT products. These options have a positive Return on Investment (RoI) of 2.5 months and 1.6 months respectively (See figure 1), placing both in the top 5 best returns a company when compared to all proposals currently in queue.
|
Both investment options yield an incredible return for the company. Although option A has a lower upfront investment of just $50K, the overall return is lower and the time to recover the investment is longer. Option B addresses both the security risk in the cloud for business applications and outbound products that will be IoT enabled.
Most of the resources used in the execution of the proposal are internal employees; this is by design. One of the major threat actors are often internal employees making mistakes. Therefore, they are one of the primary subjects in the investment. Finally, having them take an ownership stake in the overall program can only improve the outcome. |
What has Changed?
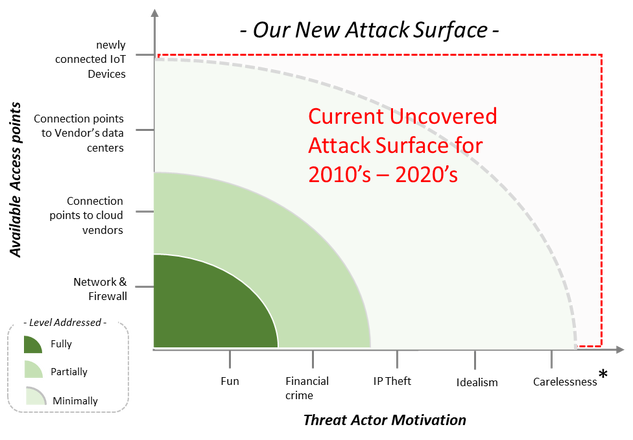
The combination of migrating business applications to the cloud, connecting products to the internet and the new threat actors has expanded the available attack surface (e.g, the risk to our organization). There are now many more points of entry and exit for the threat actors. Further, they are now more sophisticated and attack with new motivations to breach systems (See Figure 2).
Figure 2 – The new and uncovered attack surface
The combination of migrating business applications to the cloud, connecting products to the internet and the new threat actors has expanded the available attack surface (e.g, the risk to our organization). There are now many more points of entry and exit for the threat actors. Further, they are now more sophisticated and attack with new motivations to breach systems (See Figure 2).
Figure 2 – The new and uncovered attack surface
Figure 2 illustrates an attack surface comprised of two dimensions: “Threat Actor Motivation” and “Available Access Points”. The dark green at the origin depicts a typical level of coverage, which has been sufficient in the past given that most prior attacks originated from “hackers” for fun and/or profit. Additionally, the methods were typically head-on network attacks against a firewall. Over the last several years, however, companies in this space have seen threat actors motivated by theft of Intellectual Property (IP) or the IP of customers and partners. More importantly, threat actors themselves now include well-funded nation-states and other large entities with a lot of determination and resources. The new threat actors are summarized in Figures 3 and 4 below. As one examines the attack surface moving left-to-right and bottom-to-top along each axis, the color shift depicts areas where defense strategies become vulnerable to a breach. Consequently, through this program the intention is to build a culture of security across the portfolio of products and a hybrid business applications infrastructure. Appendix A - Impact to Confidentiality, Integrity and Availability (CIA) provides a table of common assets that could be compromised for discrete manufacturers and the impact this would have on the CIA triad for security.
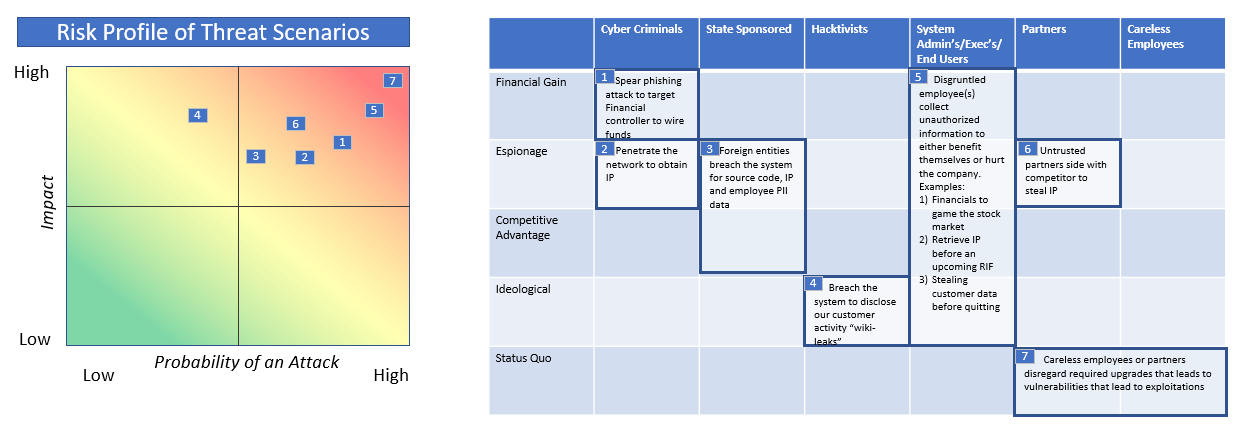
Figure 3 - The New Threat Actors and their Motivations
|
Actor |
Relationship |
Motivation |
Intent |
Region |
|
Cyber
Criminal |
External |
Financial
Gain |
Deliberate
and Competitive |
Eastern
Europe and North America |
|
State
Sponsored |
External |
Espionage
and ideological |
Deliberate,
Malicious and Competitive |
APAC
(China), Russia, Iran, Israel, U.S. |
|
Hackitivists |
External |
Ideological |
Deliberate
and Malicious |
Western
Europe and North America |
|
System
Admin’s/End Users/Exec’s |
Internal |
Financial
Gain |
Deliberate
and Malicious |
World |
|
Partners |
Internal
& External |
Financial
Gain and Competitive Advantage |
Accidental
and Deliberate |
World |
|
Careless
Employees |
Internal |
Continue
status quo or business as usual |
Accidental
and Negligence |
World |
Prioritizing an Action Plan to Achieve Greatest Protection of our Assets
…Our cyber risks fall into 3 categories. Number 1: Someone (employee) doing something stupid, number 2: Someone (employee) doing something malicious and finally, an outsider trying to hack into our systems... (Former CIO of a large printer manufacturer, 2017).
…Our cyber risks fall into 3 categories. Number 1: Someone (employee) doing something stupid, number 2: Someone (employee) doing something malicious and finally, an outsider trying to hack into our systems... (Former CIO of a large printer manufacturer, 2017).
Figure 4 - Threat Actor Capabilities
Of note, Figure 4 lists “Careless Employees” as a threat actor, which does not necessarily mean purely negligent employees. Symantec Corporation reported that accidental exposure of information is responsible for 28% of data breaches in 2013 (Symantec, 2014). Some recent profitable attack methods are “phishing” attacks and the even more profitable “spear-phishing” attacks (Rashid, 2016). Both have compromised several peer systems and will be discussed further in this report. Moreover, disgruntled employees are an emerging threat actor. Verizon recently reported that in more than 70% of IP theft cases, insiders stole information within 30 days of announcing their resignation (Verizon, 2014).
Key Take-aways and Priorities
•Start with our employees and partners. Establish a mandatory upgrade policy for all devices (laptops, PC’s, mobile phones and tablets)
•Investigate tool-sets to identify “high-risk” employees, contractors and partners. Enforce segregation of duties, audit critical practices, monitor financial status (localize)
•Increase training and coverage for key executives for spear-phishing attempts.
•Start with our employees and partners. Establish a mandatory upgrade policy for all devices (laptops, PC’s, mobile phones and tablets)
•Investigate tool-sets to identify “high-risk” employees, contractors and partners. Enforce segregation of duties, audit critical practices, monitor financial status (localize)
•Increase training and coverage for key executives for spear-phishing attempts.
Adversarial Threat Examples
Cyber adversaries are threat actors who attempt to breach our infrastructure to compromise our business through theft, denial of service, etc. usually driven by ill intent. One recent example is the Mirai Botnet attack, which is highly relevant because it could very easily have been used against our organization. Mirai is a botnet class of malware. Botnet means that it enslaves many devices and then uses them to attack a server or entire datacenters under the guidance and direction of the Command and Control server (See Figure 5).
Cyber adversaries are threat actors who attempt to breach our infrastructure to compromise our business through theft, denial of service, etc. usually driven by ill intent. One recent example is the Mirai Botnet attack, which is highly relevant because it could very easily have been used against our organization. Mirai is a botnet class of malware. Botnet means that it enslaves many devices and then uses them to attack a server or entire datacenters under the guidance and direction of the Command and Control server (See Figure 5).
Figure 5 – Mirai Botnet Attack
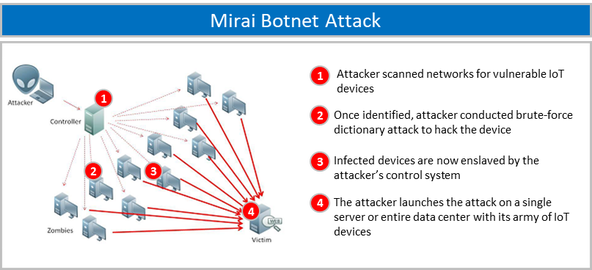
Mirai specifically targeted network routers, DVR players, baby monitors and home internet cameras. It started by scanning the internet for IoT devices manufactured by a Chinese High-Tech company XiongMai Technologies because the devices were encrypted with factory default or hard-coded usernames and passwords. These usernames and passwords created vulnerabilities because they were known manufacturer pre-sets that were either locked by the device firmware or simply were not changed by the device owner. The Mirai malware used a brute-force technique for guessing passwords (dictionary attack) based on a list of just 62 user ID’s and passwords. Once the device was compromised, the malware was planted on the device with access by the command and control server to await further instructions.
On October 16th, 2016 Mirai targeted systems operated by Domain Name Server (DNS) provider Dyn who supports some of the internet’s biggest websites, including Spotify, Twitter and PayPal. There were three attacks throughout the day that lasted approximately two hours each before they were resolved. Although the attacks accounted for only six hours, the economic damage to Dyn was significant. Bitsight reported that 8% of Dyn’s customer base stopped using their services after the attack (Weagle, 2017).
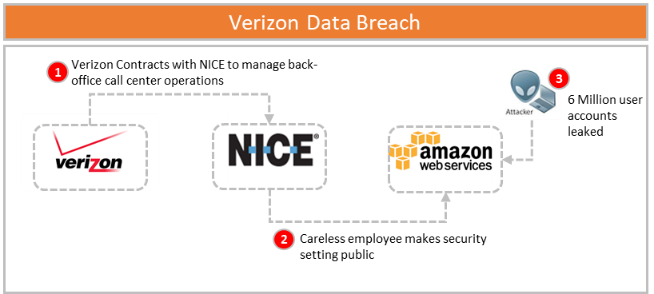
The Mirai attack could easily happen here as many organizations promote connected products and the security of their infrastructure contains multiple vulnerabilities. This proposal addresses this by establishing a governance model with vendors. In contrast to Mirai, the Verizon breach did not have the notoriety but represents a major trend that will likely emerge as an issue for any organization in the coming years. Verizon contracted with a company, NICE Systems based in Israel, to manage its back-office and call center operations. NICE uses Amazon Web Services (AWS) to store data for their customers (Verizon). As part of the initial system configuration, a NICE employee accidentally set a single security switch to “public” versus “private” (See Figure 6).
On October 16th, 2016 Mirai targeted systems operated by Domain Name Server (DNS) provider Dyn who supports some of the internet’s biggest websites, including Spotify, Twitter and PayPal. There were three attacks throughout the day that lasted approximately two hours each before they were resolved. Although the attacks accounted for only six hours, the economic damage to Dyn was significant. Bitsight reported that 8% of Dyn’s customer base stopped using their services after the attack (Weagle, 2017).
The Mirai attack could easily happen here as many organizations promote connected products and the security of their infrastructure contains multiple vulnerabilities. This proposal addresses this by establishing a governance model with vendors. In contrast to Mirai, the Verizon breach did not have the notoriety but represents a major trend that will likely emerge as an issue for any organization in the coming years. Verizon contracted with a company, NICE Systems based in Israel, to manage its back-office and call center operations. NICE uses Amazon Web Services (AWS) to store data for their customers (Verizon). As part of the initial system configuration, a NICE employee accidentally set a single security switch to “public” versus “private” (See Figure 6).
Figure 6 – Verizon Cloud Vendor Mistake
|
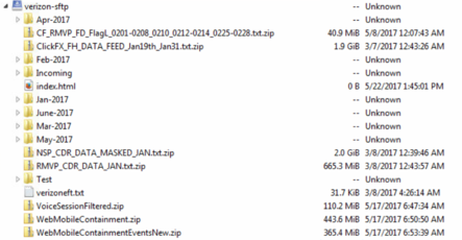
Figure 7 – Verizon FTP file directory available to the public (O’Sullivan, 2017)
|
On June 8th, 2016, a Director of Cyber Risk Research firm UpGuard discovered a cloud-based Amazon data repository was made fully downloadable and configured to allow the public to download accounts, phone numbers, PIN’s, etc. The repository’s subdomain “verizon-sftp” was descriptive enough to identify the nature and source of the data (See Figure 7).
|
The inclusion of this lesser known and far less complex case study illustrates the risk of moving to a cloud-based business model to support an IT infrastructure. Many with have and will continue to move more of IT applications to external cloud vendors and in many cases those vendors will use external data centers. A single mistake by a partner company could result in a breach that negatively impacts their brand, reputation, profit margin, and customers.
The Yahoo! attack was quite different than the previous two. This was a nation-state attack conducted by 4 Russian nationals working for the Federal Security Service of Russian Federation (FSB) formerly the KGB. It is believed they were operating under the direct orders of their employer and with support. This was a highly sophisticated team with a long history of cybercrime. They are well funded and could plan their attack and leverage the full resources of their government.The nature of the attack was to gain as many accounts as possible without leaving a trace. The method used was “forging cookies”. This allows the attacker access to an account by simply logging into it without the risk of getting caught hacking (Dark Reading, 2017).
The time they spent in each phase of the kill chain varied from a few days to many months and in a few cases, years. Two key activities took place during the reconnaissance phase; scanning Yahoo’s network for intelligence on their infrastructure and leasing servers in around the world including the United States to prevent identification. Once they penetrated the network, they continued to “reload” the weaponization phase by pursuing new targets based on the additional objectives. This was a recurring process. It is estimated there were three separate installations of malware over the course of the attack and six actions and objectives. Therefore, this was a well-planned and highly sophisticated attack.
The Yahoo! attack was quite different than the previous two. This was a nation-state attack conducted by 4 Russian nationals working for the Federal Security Service of Russian Federation (FSB) formerly the KGB. It is believed they were operating under the direct orders of their employer and with support. This was a highly sophisticated team with a long history of cybercrime. They are well funded and could plan their attack and leverage the full resources of their government.The nature of the attack was to gain as many accounts as possible without leaving a trace. The method used was “forging cookies”. This allows the attacker access to an account by simply logging into it without the risk of getting caught hacking (Dark Reading, 2017).
The time they spent in each phase of the kill chain varied from a few days to many months and in a few cases, years. Two key activities took place during the reconnaissance phase; scanning Yahoo’s network for intelligence on their infrastructure and leasing servers in around the world including the United States to prevent identification. Once they penetrated the network, they continued to “reload” the weaponization phase by pursuing new targets based on the additional objectives. This was a recurring process. It is estimated there were three separate installations of malware over the course of the attack and six actions and objectives. Therefore, this was a well-planned and highly sophisticated attack.
Cyber Threat Intelligence Plan -- Strategy and Path
The strategy for the CTIP will be composed of 3 elements and in this example, will take 1 year to fully implement. This strategy will:
The strategy for the CTIP will be composed of 3 elements and in this example, will take 1 year to fully implement. This strategy will:
- Shift the cost and the burden to the bad guys – by making it very expensive to hack our systems, products and infrastructure. The enterprise who adopts this strategy will become “the house with the Rottweilers that everyone can see” by developing an intimidating, multi-tiered, multi-level defense system composed of modern technologies, trained and educated people and leading practices and processes.
- Integrate security experts and best practices into our Product Management teams (IoT) responsible for IoT and outbound revenue facing products
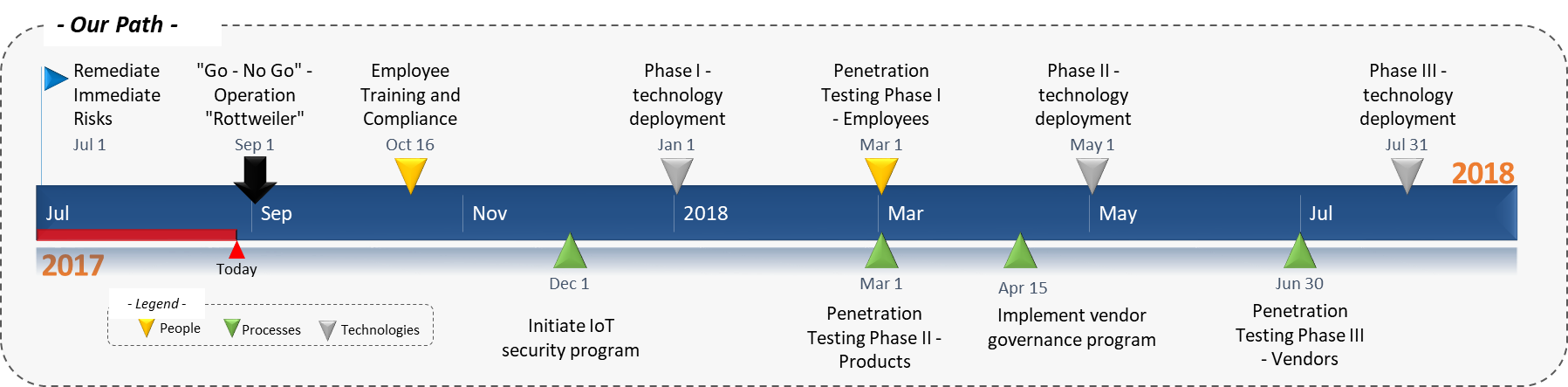
- Take a modern “threat scenario” approach that considers multiple facets; assets, threats, vulnerabilities and controls. It is our belief this strategy can be implemented in twelve months focusing on the people, processes and technologies (See Figure 8).
Figure 8 – Timeline of Activities
Assuming this project commences on July 1st, 2017. A small cross-functional team would be assembled to develop the plan, identify vulnerabilities, and remediate any significant risks following the news of several prominent and relevant cyber-attacks. “Operation Rottweiler” as the project has been named would focus on the three pillars of any business: people, processes and technologies. The deployment of this plan would be delivered in phases across all three pillars.
Conclusion
Enterprise in the discrete manufacturing sector need to adapting as the the threats evolve. This plan puts in place the necessary infrastructure to secure digital assets while creating flexibility to grow and scale to future business needs. Moreover, the approach to this plan provides a model to justify the investment with an industry standard business case methodology. In many cases, the ROI for adopting this plan ranks in the top 5 best investments an enterprise in this industry can expect to make.
Enterprise in the discrete manufacturing sector need to adapting as the the threats evolve. This plan puts in place the necessary infrastructure to secure digital assets while creating flexibility to grow and scale to future business needs. Moreover, the approach to this plan provides a model to justify the investment with an industry standard business case methodology. In many cases, the ROI for adopting this plan ranks in the top 5 best investments an enterprise in this industry can expect to make.
References
O’Sullivan, D., (2017, July 12). Cloud Leak: How A Verizon Partner Exposed Millions of Customer Accounts. Retrieved August 20, 2017, from https://www.upguard.com/breaches/verizon-cloud-leak
Rashid, F. Y. (2016, March 11). The dirty dozen: 12 cloud security threats. Retrieved August 19, 2017, from http://www.infoworld.com/article/3041078/security/the-dirty-dozen-12-cloud-security-threats.html
Symantec, (2014, April), Internet Security Threat Report. Retrieved from http://www.symantec.com/content/en/us/enterprise/other_resources/bistr_main_report_v19_21291018.en-us.pdf
Verizon, (2014, April), 2014 Data Breach Investigations Report. Retrieved from http://www.verizonenterprise.com/DBIR/2014/
Weagle, S. (2017, February 21). Financial Impact of Mirai DDoS Attack on Dyn Revealed in New Data. Retrieved August 20, 2017, from https://www.corero.com/blog/797-financial-impact-of-mirai-ddos-attack-on-dyn-revealed-in-new-data.html
O’Sullivan, D., (2017, July 12). Cloud Leak: How A Verizon Partner Exposed Millions of Customer Accounts. Retrieved August 20, 2017, from https://www.upguard.com/breaches/verizon-cloud-leak
Rashid, F. Y. (2016, March 11). The dirty dozen: 12 cloud security threats. Retrieved August 19, 2017, from http://www.infoworld.com/article/3041078/security/the-dirty-dozen-12-cloud-security-threats.html
Symantec, (2014, April), Internet Security Threat Report. Retrieved from http://www.symantec.com/content/en/us/enterprise/other_resources/bistr_main_report_v19_21291018.en-us.pdf
Verizon, (2014, April), 2014 Data Breach Investigations Report. Retrieved from http://www.verizonenterprise.com/DBIR/2014/
Weagle, S. (2017, February 21). Financial Impact of Mirai DDoS Attack on Dyn Revealed in New Data. Retrieved August 20, 2017, from https://www.corero.com/blog/797-financial-impact-of-mirai-ddos-attack-on-dyn-revealed-in-new-data.html