Conducting a DoS Attack using Metasploitable
Metasploit has a number exploit tools specifically designed for DoS attacks. The approach I took to address this query was a live attack with using a python application. This Python script implements the SlowLoris attack with a fixed number of threads opening connections with the web server. This will completely swamp an Apache server on a single machine.
Before the Attack
Before the Attack
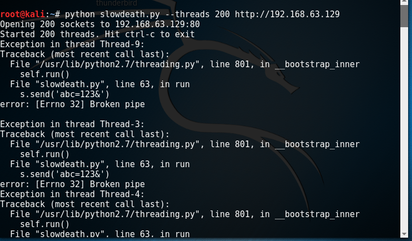
1) Launching the Attack
The program simply simulates 200 clients hitting the server simultaneously. The server is incapable of responding and is rendered useless for the duration of the attack. In this particular case, the server recovered once the attack was complete.
The program simply simulates 200 clients hitting the server simultaneously. The server is incapable of responding and is rendered useless for the duration of the attack. In this particular case, the server recovered once the attack was complete.
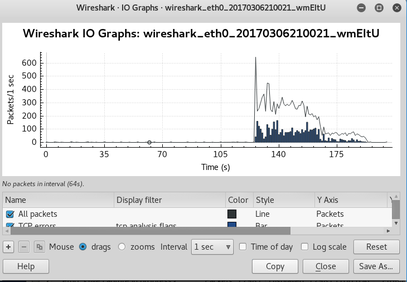
2) Measuring the Attack
The Wireshark output shows a massive spike in packet volume. The steady state prior to launching the attack was approximately 55packets/sec.
The Wireshark output shows a massive spike in packet volume. The steady state prior to launching the attack was approximately 55packets/sec.
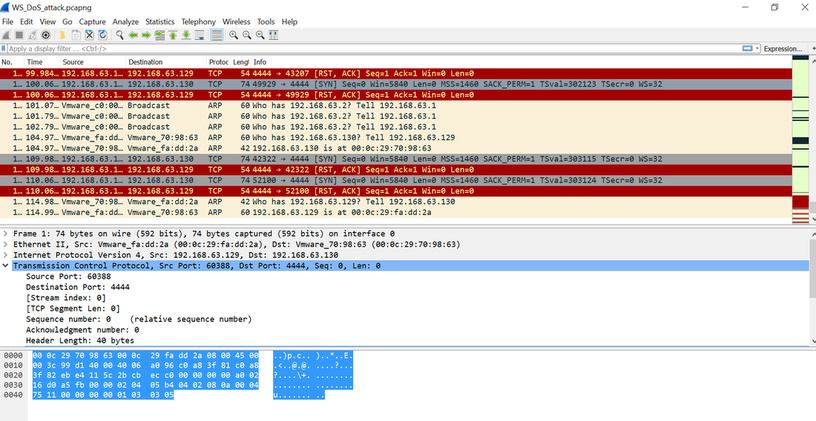
3) During the Attack
Begin by going to a benign URL (sans.org). Although there was no spooky or demonic message during the attack, there was "just" a denial of service (DoS). The browser continued to “spin” and the server could not return the request from the client. Until python program completed.
Begin by going to a benign URL (sans.org). Although there was no spooky or demonic message during the attack, there was "just" a denial of service (DoS). The browser continued to “spin” and the server could not return the request from the client. Until python program completed.